
Telenor presents high-level information about the capabilities needed to develop an organisation’s overall security posture in terms of the overall maturity of a security operations centre (SOC).
An SOC builds on security controls as defined in the detection area of Defendable Architecture and how they can be most effectively used. After completing the Design and Build phase, it’s time to “run it”, i.e. as in operating it, but also to “defend it” which in this context is to conduct security operations to discover hidden threats and to respond to them in an effective and timely manner. Remember, these controls have little value if they are not operated and maintained by competent people who have clearly defined processes for both operations, change management, detection, and incident response.
So, while this article is technology focused, it should be kept in mind that the individuals manning the security functions make a significant impact to the expected outcome of the security operations function. The SOC should therefore, in addition to clearly defined roles and responsibilities, have formal description of required and desired competence and competence development plan for each role.
Defender incident response abilities are similar to the different tiers of threat actors along with their offensive capabilities that were shown by the threat actor pyramid in our article on defendable architecture. A similar pyramid can be defined for the defenders along with required defensive capabilities present within the organisation. This gives an overview of what actions the SOC is actually capable of performing.

Security operations abilities are based on what the operations teams are capable of performing of actions for incident response and is referred to as “the incident response hierarchy of need”. What actions the SOC is able to perform plays directly into the ability to mitigate the different levels of threat actors in an efficient way. These abilities are built up by the different defined defensive capabilities in the form of tools and technologies and supported by effective processes.
There are different sets of SOC processes and schools of thought, but current trending points towards using so-called OODA (observe, orient, decide, act) loops along with security automation as described in a good article by Jurgen Visser, all while operated by competent people. The cited areas of technology, people, and processes all need to progress for security operations teams to be able to develop better abilities as required in incident response.
To develop the SOC, it is recommended to measure and stage the introduction of detection capabilities along with the required supporting processes and competencies and create a clear roadmap to move up in the hierarchy of defensive capabilities. To put it simply: learn to walk before you run. From the figure above it is possible to see that without a proper asset inventory, monitoring, and detection capabilities, it will become very difficult to build any kind of advanced response abilities and go threat hunting for instance. Having a proper foundation becomes important when wanting to address the higher tiers of threat actors since the implementation of the more advanced capabilities relies on the lower but foundational capabilities to be properly implemented and operated first.
One also needs to consider the sequencing of tools, processes, and organisation. It is highly recommended to focus on the organisational aspects and staffing first, as one can expect that competent people will be able to identify and implement capable tools and processes in a more effective and efficient manner.
The dependency and sequenced implementation of capabilities are directly connected to the stepwise increased ability to mitigate threat actors. This will influence the mitigation efficiency as shown in our previous article about defensive capabilities and measured against the SOC maturity shown below. In any case, it will be necessary to adapt this to the existing capabilities and particulars of each individual organisation unit to create a specific implementation plan.

So, how is a SOC’s effectiveness measured? Similar to the capability levels of the defined security controls described in the earlier article with their implementation levels, typical capability steps of a Security Operations Centre are also listed as a set of incremental steps. The model shown here is based on that from the SOC-CMM framework. The defined levels follow the maturity levels which are used to measure an organisation’s overall security maturity.
SOC maturity level 0, Blind
At this level, the focus is only on preventive measures. Responsibility for detecting and handling incidents is not defined and resources are not present. Few if any of the defined capabilities for detection to perform security monitoring are implemented.
Detection capabilities implemented for this maturity level
None, preventive only
Average Detection capabilities process maturity
Initial
Detection capability people & skills maturity
Initial
Any organisation at this level would certainly fail an audit or the most basic of compliance checks and would not be considered professional to its customers and be in violation of most countries’ privacy regulations. Consider this level for reference only, it’s not possible to get any worse.
SOC maturity level 1: Performed
At this level, security is performed on an ad-hoc basis. The ability to protect company assets is considered to be limited.
High level policies in place
Key Processes (Patch, Vulnerability, Credentials) Performed Ad-Hoc
Some detection capabilities are implemented.
The security operation is mandated in the company as a function, but is considered a non-important capability that receives minimal effort. Central security monitoring is in place, but only collecting logs from a small subset of assets and are not regularly maintained. Incidents are discovered only through pre-set rules and indicators on an ad-hoc basis, and no formal process exists for incident handling.
Detection capabilities implemented for this maturity level
vulnerability scanning: basic
endpoint detection and response: basic
logging and auditing: basic
IDS/IPS sensors: basic
Detection capability process maturity
developing
Detection capability people maturity
developing.
SOC maturity level 2: Planned
At this level, security is performed and based on structured plans. The ability to discover basic incidents and lower-tier threat actors are present.
Security capabilities include certain security specialists
Minimum security requirements implemented in processes in IT infrastructure (e.g., Patch, Credentials)
Most detection capabilities are implemented at a basic level and Basic Monitoring is in place.
Reactive response is conducted.
The security operation is compliance-focused only. No security operations charter and champions exist. There are no existing continuous improvement activities, and capacity and competence are at a required minimum. Logging is expanded to cover critical assets, and some additional monitoring tools are introduced. Forensics is not performed, re-imaging is the main cause of action. The incident response process exists on paper, but is not followed consistently.
Detection capabilities implemented for this maturity level:
vulnerability scanning: basic
endpoint detection and response: basic
flow based network monitoring: none
logging and auditing: basic
IDS/IPS sensors: basic
Detection capability process maturity
defined
Detection capability people maturity
defined.
SOC maturity level 3: Managed
Security systematically managed. Ability to protect against regular incidents.
Security Risks are identified and managed. Security management system implemented
Preventive defensive capabilities ensuring resilient technical security infrastructure
All detection capabilities at a basic or intermediate level are implemented
Advanced Security Monitoring established. Can identify advanced threats
The security operation is considered important for the business.
Multiple tools in the form of detection capabilities with regularly updated threat intelligence feeds are introduced, and asset coverage if these capabilities are approaching 100%. Incident handling follows a structured and measured process. Clear responsibilities are defined and anchored, and there are a dedicated department and individuals with competence and capability to handle security monitoring and incident response 24/7. Basic forensic analysis is performed on selected incidents. Threat hunting is carried out on an ad-hoc basis. Performance is measured. At this level, a company is able to handle most incidents up to tier 4 threat actors, but not APTs (tier 5 and above).
Detection capabilities implemented for this maturity level:
vulnerability scanning: intermediate
endpoint detection and response: intermediate
flow based network monitoring: basic
logging and auditing: intermediate
IDS/IPS sensors: basic
Detection capability process maturity
managed
Detection capability people maturity
managed.
SOC maturity level 4: Measured & controlled
Security capabilities are measured. The company has the ability to protect against and mitigate advanced threats.
Security organisation with specialist functions
Infrastructure segmented and controlled
Key processes measured and controlled through KPIs and metrics.
Security operation is delivering clear value to the business by effectively detecting and handling incidents before they can harm the business. A comprehensive and integrated toolset is used, managed by security engineering. Threat hunting finds incidents on a regular basis. Advanced forensic capabilities exist and are in regular use. A structured process exists to improve preventive measures from incident learnings. Threat intelligence provides valuable input to detection capabilities. Able to handle APT incidents.
Detection capabilities implemented for this maturity level:
vulnerability scanning: intermediate
endpoint detection and response: advanced
flow based network monitoring: intermediate
logging and auditing: intermediate
IDS/IPS sensors: advanced
Detection capability process maturity
measured
Detection capability people maturity
measured.
SOC maturity level 5: Tailored
Security subject to continuous improvement. Effectively protect and mitigate advanced threats.
Security fully integrated into all parts of the organisation
All infrastructure built with preventive capabilities implemented from the start, with automated security supported by artificial intelligence and machine learning.
Security is considered to be a fundamental capability with high criticality for the organization which takes the lead among peers in the area. Security operation has a high degree of automation, and continuous improvement processes are working well. Able to detect and evict most threat actors, including APTs, before they gain a foothold supported by IT architecture design.
Detection capabilities implemented for this maturity level:
vulnerability scanning: advanced
endpoint detection and response: advanced
flow based network monitoring: advanced
logging and auditing: advanced
IDS/IPS sensors: advanced
Detection capability process maturity
optimised
Detection capability people maturity
optimised.
The sweet spot for a mature SOC is considered to be at either high 3 or a low 4, which should be both an acceptable and achievable target for a regular company. The approximate average seen across different sectors and verticals is assumed to be around 2.75 based on input from consultancies helping companies to mature their SOCs. This is quite low and is one reason why cyber-crime is beginning to have such a large impact on society as a whole. On the other hand, some sectors constantly on the front line facing threats and under regulatory risks, such as the finance sector, are on average more mature (typically around 3.5). The more security conscious industry sectors, such as the defense industry or military are above that number, mainly due to having a proper security mindset fully integrated into all aspects of their organisation.
To get started, the first step is to perform a gap analysis and make a phased improvement plan. It is recommended to set specific targets for improving maturity scores over a one to three year period, with concrete milestones and deliveries, similar to the staged implementation of the capabilities. With the assumption of starting at level 0 or 1, achieving level 3 or above in SOC maturity will take a significant amount of time, budget, and focused effort.
How can Security Operations Threat mitigation efficiency be measured? Similar to the defensive capabilities described previously, the maturity of the security operations centre, the tools, processes and the number of competent resources available play directly into the ability to mitigate the different levels of threats:
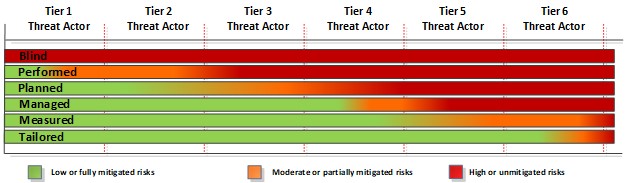
Building on the implemented defensive capabilities and tools, the SOC will be able to detect more capable threat actors. While the purpose of the implemented preventive security controls is to prevent threat actors from breaching the infrastructure, the main purpose is to be able to detect any threats that actually do. With thousands of components in the average infrastructure, a breach will inevitably happen sooner or later. When it does, it is necessary to have all tools, capabilities, processes, and competencies in place to support an effective incident response process to evict them before any serious damage is caused to the enterprise.
Stay safe, stay secure.