The Nordic threat picture
As the telecom operator with the largest footprint in the Nordics, Telenor faces a uniquely complex threat landscape. In this chapter, we examine the current Nordic threat picture through the lens of Telenor’s security experts, highlighting how critical infrastructure, mobile networks, and broad customer relationships make the telecom sector a prime target. From destructive cyberattacks to AI-driven scams and supply chain vulnerabilities, we explore the tactics and threat actors shaping today’s risks, and the importance of resilience, preparedness, and collaboration across industries and society.
Telecommunications – a prime target in an evolving threat landscape
The telecommunications industry is considered an attractive target for threat actors. Most operators have access to a substantial amount of sensitive data and operate as a digital gateway to other audiences and industries through their customer base. 5G and private networks are security enablers but as critical services such as mobile connectivity, positioning, and data services are vital for society, they are also particularly attractive targets.
As a result, the possible attack surface is larger in the telecommunications industry than most other industries. Companies, like Telenor, own, operate, and secure critical services and infrastructure that most people depend on in their daily lives. Lessons learned from telecom operations in Ukraine also show the importance of preparation and resilience in face of worsening security situations.
Telenor is one of the largest digital service providers in the Nordics, delivering telecommunications, content, and data services. This increases the threat to Telenor in general, as a symbolic target and due to our broad customer relationships. Our interdependencies with other companies that deliver critical services both enables us to cooperate on security and emphasise the importance of a strong security posture throughout society.
The threat landscape must be viewed holistically, taking into consideration not only Telenor’s security challenges but also the intentions of potential threat actors targeting Telenor's customers, whether private customers, corporate customers, businesses, or national authorities. This also requires a clear recognition of the assets and values at risk for our customers, and our role in safeguarding these.
In Telenor, we systematically gather security information from national authorities, open-source reports, commercial intelligence services, and our own data and internal threat communities. Another important source is the public assessments made by the Nordic national authorities, both in terms of the security situation the region is facing and specific threats directed at critical infrastructure. This broad approach ensures we maintain a comprehensive and up-to-date understanding of the threats facing both Telenor and the wider industry.
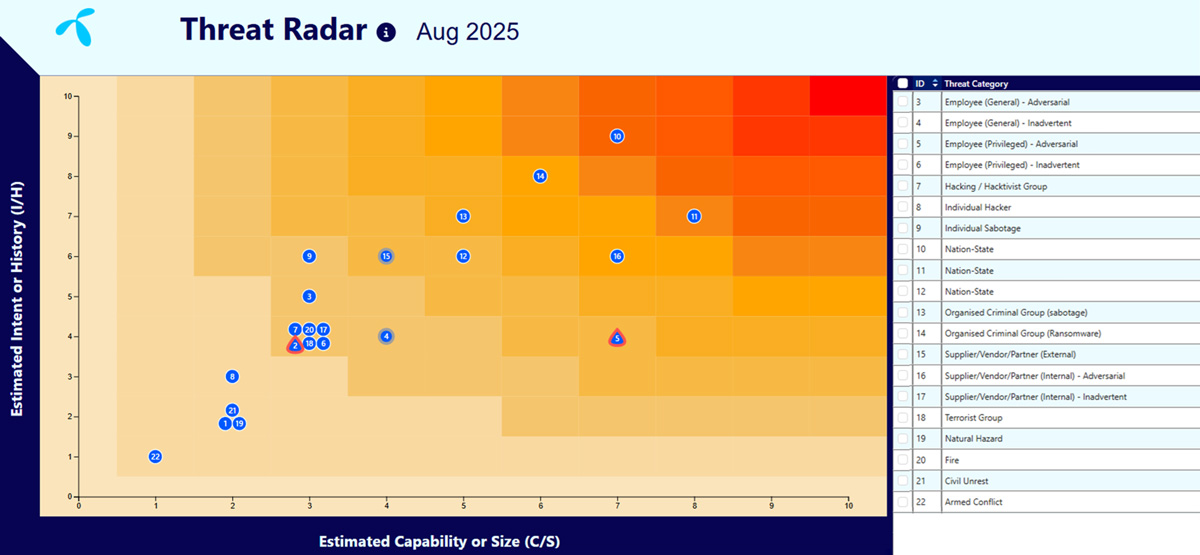
To stay ahead of evolving threats, we have developed a Threat Radar that consolidates intelligence from multiple sources to assess adversaries’ intent, capabilities, and tactics. This gives us a clear view of emerging trends, enables us to prioritize controls, and turns the threat landscape into actionable insight for leadership across all regions and business units. For a company that owns and operates critical infrastructure, the inability to read and respond to the threat picture could have severe consequences not only for Telenor but also for societal resilience in the Nordic countries, which is why we place strong emphasis on continuously assessing and updating our understanding of the threat environment.
The big picture impact on telecommunications and our customers
In recent years, it has become increasingly clear how dependent society is on well-functioning and stable infrastructure and how attractive these assets are to threat actors. Protection is therefore crucial for national security, especially in an era of increased digitalisation and reliance on technological solutions.
The European security environment has in recent years been characterised by significant change and increased tension. Russia's invasion of Ukraine has reinforced the need for a unified European defence, which led Finland and Sweden to apply for membership in NATO. This shift is changing the security architecture of Northern Europe and has strengthened the Alliance's position in the region. At the same time, there has been an increase in hybrid threats, including cyberattacks and disinformation campaigns targeting critical infrastructure. An escalation in drone incursions in the Nordic countries in late September 2025, near airports, naval installations, military bases, and energy facilities, has highlighted how new methods of surveillance and potential sabotage are being used to test vulnerabilities in civilian and military preparedness across the region.
The security situation we are facing requires companies such as Telenor, along with other businesses delivering critical services, to take practical measures to review contingency plans, practice, interact and prepare for possible scenarios. This is part of our social responsibility under the Total Defence concept, and it highlights the need for close cooperation between the Nordic countries.
We must be prepared to manage prolonged periods of uncertainty, during which hybrid threats to the Nordics could challenge our ability to deliver stable and secure services in various scenarios.
Scenarios with increased probability that Telenor must prepare for:
Destructive cyberattacks
Sabotage of digital or physical infrastructure
Influence campaigns that may target businesses or business leaders
Intelligence operations, including mapping physical and digital infrastructure, and recruitment of insiders
Organised crime targeting infrastructure, digital attacks for profit such as ransomware
Technically advanced internet scams targeting consumers or employees
Intelligence threat towards telecommunication infrastructure
We must be prepared for the fact that the High North and the Baltic Sea areas will become more militarised in the long term. As a result, Telenor, through its role in Total Defence and as a provider of critical services and infrastructure, is likely to attract greater intelligence interest from Russia. This can materialise in the form of increased intelligence activity towards our infrastructure, in particular, infrastructure or services that support NATO and the Armed Forces' activities. Infrastructure in the High North, and infrastructure across borders by land or sea in the Nordics, could also be vulnerable targets for mapping and potential sabotage by Russian actors.
Hostile intelligence operations can span all domains, including insider threats and recruitment attempts. It is particularly important to continue to protect critical information about our infrastructure in the High North and the Baltic Sea. Security is thus given high priority when entering into contracts for the development and modification of infrastructure.
In addition to threats directed at physical infrastructure, the theft of customer data is emerging as one of the most serious espionage risks facing the telecommunications sector. Operators like Telenor manage large volumes of call data, location information, and traffic patterns, which, if breached, can provide state-backed actors with unique opportunities to track political leaders, public authorities, business executives and other persons of strategic interest. Such data is of high value for recruitment, mapping of networks, and broader influence operations. State-backed actors, in particular, have shown an interest in exploiting such information. Protecting customer data against espionage-driven theft must therefore be prioritised to the same degree as protecting critical infrastructure.
What do we need to protect against intelligence threats?
Own preparedness, including plans, routines, personnel and any changes in operations during incidents or alternative locations
Others business emergency preparedness functions that your business contribute to
Vulnerabilities related to physical or logical infrastructure – especially related to critical components
Information relating to supply and re-supply chains
Fault correction times related to important infrastructure and services, and details of collaboration and deliveries to other critical infrastructure
Plans and sketches detailing existing, planned, and any new critical infrastructure
The importance of a secure supply chain
Increasing international tension and a significantly deteriorating security situation mean that companies in critical and important sectors in the Nordics should strengthen their work in the areas of security, emergency preparedness, and resilience. However, not all suppliers can quickly raise their standards due to cost constraints, which increases overall supplier risk. This has resulted in a greater need to keep track of suppliers, set requirements for security levels in collaboration, and advise them on how to improve security awareness and implement stronger security measures.
Even if vulnerabilities pointed out by the authorities do not directly affect one's own workplace, it can represent an indirect vulnerability if it affects some suppliers or subcontractors. This requires a dialogue with suppliers to ensure that they are aware of their potential vulnerabilities and handle them in a responsible way.
Major geopolitical tensions may also result in suppliers, who are subject to government control or influence, delaying or denying delivery of goods, updates, or other contractual obligations as part of a broader political strategy.
There is a persistent risk that some suppliers, unknowingly, or even consciously, do not carry out, for example, critical security updates. There are cases where some suppliers have been suspected of adding hidden backdoors or failing to address critical vulnerabilities, as this can provide an entry point that can be exploited if needed.
General recommendations to enhance supplier security:
Closer follow-up, security collaboration with (and control of) suppliers
Ensure common situational awareness and security understanding with suppliers
Ensure suppliers have a structured vulnerability management process
Exercising contractual right to audit
Require the suppliers to have a system for systematic penetration testing
In cases where there is uncertainty about vulnerabilities in supply chains, these issues should be clarified and subjected to risk assessment
Pre-positioning for sabotage against telecommunications
State threat actors, especially from countries such as Russia and China, are actively positioning themselves for possible sabotage against businesses and infrastructure in Western countries. Their methods include cyber operations, intelligence operations, and physical infiltration. Infrastructure such as subsea fibre cables are vulnerable to physical sabotage. Russia has previously shown a willingness to carry out such operations to destabilise the region and send political signals to the West. Access to telecom operators provides strategic intelligence to China, especially in the context of prepositioning China for future conflicts - both politically, militarily, and economically.
Threat actors who seek to infiltrate critical systems often do so to map, collect sensitive information and/or prepare acts of sabotage. Such operations may include planting malware that can be activated to disrupt or destroy infrastructure at a later date.
The threat of sabotage against companies operating critical infrastructure in the Nordics is not only a threat to the company itself. The dependencies between companies or sectors within critical infrastructure in the Nordics are large - and the consequences of sabotage against one company can quickly have major ripple effects. Cooperation between the state and companies in critical infrastructure, as well as between companies themselves, is critically important.

Nordic perspectives on hybrid threats and critical infrastructure resilience
The Norwegian Intelligence Service assesses that "Russia will strive to carry out this type of operation without being held responsible, and in particular seek to exploit uncertainty related to the fact that damage to underwater infrastructure may have natural or unintended causes. Particularly serious is the threat to communication cables linking Europe and the US and energy supplies such as gas pipelines" and that "Russia continues to develop military capabilities to threaten Western infrastructure underwater. " Subsea fibre cables are crucial for internet and communication services in the Nordic region, but have proven to be vulnerable to both accidents and potential acts of sabotage, as described in Chapter 5 in this report.
To counter the threat of sabotage, the Norwegian Security Authority (NSM) recommends "prioritising backup solutions and resilience, surveillance and detection measures, as well as practicing contingency plans. This is to ensure rapid response and recovery in the event of a loss of critical input factors such as power, transport, internet, water or position, navigation and timing (PNT). " In addition, NSM also advises establishing the necessary contingency arrangements for repair capacity, spare parts, and personnel, alongside regular reviews and rehearsals of routines for emergency preparedness, practising the loss of critical input factors. Ultimately, this is a matter of resilience: the ability to withstand attacks, operate under duress, and restore functionality quickly after an incident.
Finland’s experience with hybrid threats has become increasingly relevant in the current security environment. According to the Finnish Security and Intelligence Service (Supo), Russian sabotage efforts in Europe are most often linked to Russia’s (GRU) military intelligence service, with the purpose of instilling fear and undermining Western support for Ukraine. Since the invasion of Ukraine in 2022, several European countries have experienced acts of sabotage attributed to Russian intelligence, including arson and attacks on infrastructure. Russia has increasingly relied on intermediaries, such as criminals or financially motivated individuals, to carry out these operations. These proxies are typically recruited through social media and are not particularly professional, often targeting symbolic or less well-protected sites.
The Swedish Security Service (Säkerhetspolisen) also reports that the international security situation continues to affect Sweden, with foreign powers, primarily Russia, China, and Iran, exploiting vulnerabilities in information, personnel, and physical security. In the past year, Sweden has experienced several incidents classified as hybrid threats, including cyberattacks, drone incidents, physical sabotage, and cable damage in the Baltic Sea. Russia, in particular, has taken an increasingly offensive stance, seeking to undermine European support for Ukraine and circumvent sanctions, while also finding new methods of intelligence gathering after the expulsion of its officers from Europe.
The Swedish Security Service highlights that foreign powers are using illegal intelligence activities, influence operations, cyberattacks, theft of technology, mapping, and threats against opponents to destabilise Sweden and Europe. The Service also notes an increased Russian risk appetite, with explicit threats of sabotage within Sweden. Sweden’s recent NATO membership and the expansion of Total Defence have introduced new critical assets and potential vulnerabilities, requiring continuous adaptation of national protection measures.
The Danish Security and Emergency Management Authority (Styrelsen for Samfundssikkerhed) has also voiced its concerns about vulnerabilities to critical infrastructure. In early 2025, the authority elevated the threat level against the telecommunications sector to “very high”, due to an increased risk of cyberattacks, sabotage, and other hybrid threats that target Denmark’s digital backbone . This assessment highlights the importance of telecommunications networks for societal resilience and shows that they are potential targets in the current security climate, requiring greater protection and preparedness.
General recommendations:
Rehearse relevant scenarios where the loss of critical functions is central. This is especially true for scenarios where we have a loss of deliveries due to destructive activity – both physically and logically.
Prioritise detecting state actors. Destructive logical sabotage by state actors often means that a threat actor has already had access to systems and has been able to map activity and pre-position itself in it.
Focus on protective measures that will make it more difficult and time-consuming to carry out successful ransomware attacks, because it is seen that this type of attack can be used as a tool in hybrid warfare
Maintain an overview of which systems are connected to networks is critical in order to know that we are monitoring what we should be monitoring, and to be able to prioritise between systems when needed.
In addition to having a low threshold for reporting possible safety-threatening incidents, we recommend keeping an eye on the following related business operations:
What does “normal” look like? Are there deviations outside our normal picture? Is this an "abnormal" error? If so, what happened?
What is the frequency of this type of deviation? Do we see that this is something that happens more often than usual? Why are we seeing an increase?
What is the consequence of the error? Does this have greater consequences than we have previously seen (either for our own operations or nationally)?