Emerging threat methods across the Nordics
In 2025, we face a more complex and multifaceted Nordic threat landscape. Attacks no longer follow a single path – they target both consumers and businesses, PCs and mobile devices, local systems and cloud-based platforms. This chapter explores the methods used to target Nordic individuals and organisations.
Digitalisation has brought enormous progress to both society and business – but it has also made us more vulnerable. When we are deeply reliant on digital systems for everything from electricity and healthcare to finance and communication, any disruption can have far-reaching and critical consequences.
This is a growing concern among the Nordic population. A 2025 survey on household awareness and behaviour related to personal preparedness, conducted by the Norwegian Directorate for Civil Protection and Emergency Planning, showed that nearly half of respondents (47%) said they are more worried about potential cyberattacks targeting control systems over the next five years than they are about terrorist attacks (35%) or acts of war on Norwegian soil (29%).
At the same time, the threat landscape has become more challenging. Different threat actors may collaborate more closely, or act independently as part of the same attack. What begins as a breach in one system or at a single company can quickly escalate, causing ripple effects that impact far beyond the original target.
With a mix of established attack methods and new AI-driven tools, it’s no longer certain who you’re communicating with or which sources can be trusted. As work processes and routines evolve faster than many organisations and employees can adapt, threat actors are quick to exploit the “cracks” that emerge.
And it’s not getting any simpler. Attacks no longer follow a clear path. They cut across roles and domains – between consumers and businesses, between PCs and mobile devices, between local infrastructure and global cloud services. Where we once drew clear lines between personal and professional risk, or between technical and human vulnerabilities, we now face blurred boundaries and attack patterns that are increasingly difficult to detect using existing security solutions.
All of this makes it harder to understand who is attacking, how the attacks are carried out – and what the actual target is.

That’s why the new threat landscape demands a holistic approach, covering everything from platform choices and authentication to human behaviour and organisational preparedness.
Read on for a closer look at the methods currently being used against Nordic organisations and individuals, and how, in some cases, they are connected.
How Nordic organisations are being targeted
Mobile phones: An underestimated risk
Today, the mobile phone is an essential tool for most of us, both professionally and personally. It provides easy access to virtually all accounts and systems, whether it’s email, messaging, social media, or company data stored across various cloud platforms.
Key threat methods covered this year:
Mobile phones: An underestimated risk
Information stealers: Gathering as much data as possible without leaving a trace
Access gained through login credentials
Clickfix and FakeUpdates: A new level of social manipulation
QR codes, voice phishing, and cross-platform attacks
Attacks-as-a-service: Ready-made attack packages
Vulnerable supply chains and embedded malware
AI agents and automated fraud
Increasing personalisation of attacks
AI is not just a threat – it’s also part of the defence
Yet, in many cases, employees’ mobile phones are less protected than company-managed PCs. While PCs are typically secured with endpoint protection (EDR), policies and logging, many organisations, even large ones, lack equivalent security mechanisms for staff mobile devices.
This makes the mobile phone, and by extension the organisation, a vulnerable target. Attacks can persist over long periods without being detected.
Most successful attacks today still begin with “traditional” phishing techniques. On mobile devices, this often takes the form of smishing (fraudulent SMS), where the recipient clicks a link in what appears to be a normal message and, for example, enters valid login details on a fake website.
Session data, cookies, or login tokens can now be more easily captured from mobile devices using various tools. These can be misused to grant unauthorised access. In some cases, criminals have also deployed “zero-click” code to gain access to victims’ phones. This is typically distributed via image attachments or other content that loads automatically in emails or SMS messages, and then executes malicious code on the device. As the name suggests, this means the victim’s phone can be exploited without them clicking anything, often due to vulnerabilities in software or the operating system. While such attacks were previously used against journalists, politicians, and high-profile targets, they are now being deployed more broadly.
When so much functionality and access is concentrated in a single device, where security measures are often limited, the mobile phone becomes one of the most exposed, and therefore most effective, entry points to sensitive data and systems. Attackers can also maintain persistent access to systems without using malware or other methods that might be flagged by the organisation’s security systems.
Telenor Norway: Over one billion digital threats in the first half of the year
During the first half of 2025, Telenor’s security filters blocked just over one billion unsafe websites and attempts at digital crime in Norway alone – a figure that illustrates both the scale and complexity of today’s threat landscape.
Of these, 974 million incidents were linked to web traffic, 25.3 million involved SMS, and 18.7 million were attempts at fraudulent calls.
The impact of the security filter introduced jointly by Norwegian telecom operators in November 2024 is particularly noticeable in terms of fraudulent calls. The number of these types of calls is gradually declining month by month, demonstrating the value of coordinated industry-wide measures in the fight against digital fraud. Thanks to Telenor’s security filters, very few scam SMS messages now reach end users, especially in comparison to previous years.
However, threat actors are proving highly adaptable. As it becomes harder for them to succeed with scam calls and messages via mobile networks, we’re seeing a shift towards online communication platforms such as iMessage (iPhone), RCS (Android), WhatsApp, Messenger and Signal, alongside consistently high activity via email and social media.
This shift isn’t necessarily about attacks becoming more targeted, but rather about threat actors choosing platforms where filtering and blocking are less common or harder to implement. These are channels where telecom operators have limited opportunity to intercept fraud attempts, which gives threat actors more room to operate.
Telenor Linx, which delivers international voice, user authentication, data roaming, and direct carrier billing globally, stated in September 2025 that they have seen a 30 percent increase in blocked calls over the past year. One-third of all calls Telenor Linx handle are now blocked and this number is increasing as detection systems are working harder than ever before.
All of this – combined with the points further below – create a growing need for increased awareness and knowledge among the general public, as well as continued development of tools and techniques for detection and response by security providers like Telenor.
Information stealers: Gathering as much information as possible, without leaving a trace
Once an attacker has gained access to a compromised device, the goal is often to extract as much valuable information as possible, quickly and without being detected. For this task, so-called information stealers such as Lumma, RisePro, StealC, Vidar and RedLine have become essential tools for cybercriminals. These tools can identify and collect large volumes of sensitive data, including usernames and passwords, browser data, cryptocurrency wallets, and login credentials stored in browsers and password managers.
Collected data is packaged and exfiltrated, then either used for further attacks or sold on the dark web as complete logs of an organisation’s or individual’s digital life. Many types of information stealers are spread through fake email attachments, free software, bogus updates or malicious browser extensions, and affect both individuals and businesses. By infecting a large number of devices, criminals can systematically sift through the data to identify valuable information – or sell bulk logs as a bundle.
The use of information stealers rose sharply in 2024, and that growth has continued into 2025 despite coordinated operations against leading tools like Lumma and RedLine. This surge can be explained by the fact that access from a single user can serve as a gateway to further compromise. Once passwords, cookies and usernames have been extracted, attackers can move deeper into an organisation’s systems, for instance, logging into Microsoft 365, AWS, Slack or other SaaS platforms. This can happen without triggering any alarms, especially if the login is routed through a proxy or VPN service (making it appear as though the attacker is logging in from a Nordic country).
A campaign that spread throughout summer 2025 involved a fake free programme for editing PDF files.
It was distributed at scale via Google ads and a dozen domains, all appearing to be legitimate. Users who downloaded the programme were presented with what looked like a genuine PDF tool, but in reality, it was a front for underlying information stealer code that remained dormant for nearly two months before being activated.
By exploiting Windows’ built-in system for protecting and managing sensitive information (DPAPI), the programme extracted stored usernames, passwords and browser cookies. It also checked which security programmes were installed and, in some cases, connected the device to a proxy network to conceal the attackers’ additional activity.
Each week, Telenor’s security team observes extensive logs containing passwords and login cookies from users being put up for sale on Russian forums, illustrated below by an example from Norway. Typically these are priced at around 10 dollars for full access to all of a person’s user accounts.
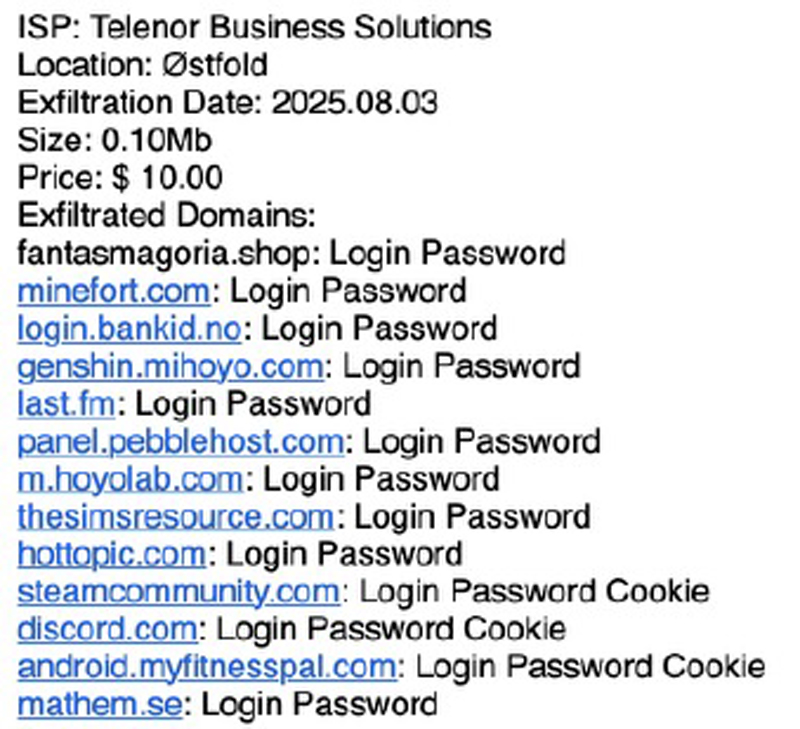
Access gained through login credentials
As more and more companies move their business data from on-premises solutions (on local servers) to the cloud, the challenges become even clearer, especially as attacks increasingly occur through login credentials rather than digital intrusion through a breach.
Attackers can make use of login details that have been purchased on the dark web or obtained through phishing or information stealers.
At the same time, there are other highly effective attack techniques that don’t require passwords. By exploiting the OAuth protocol – a standard that allows apps to access accounts without sharing passwords (such as “Sign in with Google”) – attackers can gain access to a user’s data without ever knowing their password. They build convincing phishing campaigns, often using replicas of genuine login pages from Microsoft, Google or Amazon, and prompt the user to approve access to, for example, an email account by clicking “approve” on a security request.
If the user is persuaded and approves the fake request, the attacker is issued a valid OAuth token, giving them full access to the user’s account on platforms such as Microsoft 365, Google Workspace or AWS, again without installing malware or triggering any security alerts.
In these cases, there are no signs of a breach that would activate endpoint security solutions. At the same time, many organisations are reluctant to invest in costly cloud logging, or such solutions are fragmented or entirely disabled. This gives attackers almost unrestricted operational freedom, with full access and minimal risk of detection.
Once inside the systems, many threat actors choose to use legitimate tools such as PowerShell, WMI, and Windows Scheduler to carry out malicious actions, rather than installing malware. This type of activity, known as “living off the land”, appears as routine server administration and often goes unnoticed by traditional security systems. The result is persistent attacks that are harder to detect or investigate, especially in cloud or hybrid environments.

Clickfix and FakeUpdates: A new level of social manipulation
Regardless of the attack methods used or the technologies behind them, nearly all successful attacks share one common trait: they rely heavily on social manipulation.
We are tricked, under false pretences, into taking an action that gives attackers access or information they wouldn’t otherwise obtain.
Over the past year, this tactic has been put into practice through Clickfix, a method first observed when Russia used it early in the war against Ukraine. Criminal groups have since adopted the same approach, and Clickfix has proven just as effective against businesses.
In short, this method involves sending the victim a fake error message. Immediately afterwards, the victim is presented with a quick “solution” that allows them to fix the issue themselves, without bothering the IT department or others. All it takes is accepting the error message, ticking a CAPTCHA box, or clicking through a few simple steps. What appears to be a quick fix for a (non-existent) problem is actually a prompt for the victim to paste code into a dialogue box, which then runs commands on their device. In doing so, the victim unknowingly grants the attacker access to systems and sensitive information.
In addition to Clickfix, the FakeUpdates malware was actively deployed in early summer 2025. Victims are told they need to update their browser or software to avoid security risks. If they accept the update, an information stealer is installed instead.
Schools, universities, and research institutions are attractive targets due to their large user bases and cultural emphasis on openness, a core principle in this sector making it more vulnerable.
Clickfix and FakeUpdates follow the same pattern as other modern attacks: they play on emotions, blur the lines between users’ professional and personal lives, and take place in environments where security policies aren’t always strictly enforced, such as home offices, hybrid setups, or the transition zones between personal and work devices. This makes the technique both relevant and effective, as it primarily bypasses human defences.
QR codes, voice phishing, and cross-platform attacks
QR phishing, or “quishing”, has proven to be one of the most versatile methods for bypassing traditional security systems. This type of attack often combines multiple devices, channels, and contexts.
In recent years, we’ve become accustomed to scanning QR codes in restaurant menus, advertising campaigns, and banking services, often without considering that a QR code is simply a shortcut to what is, essentially, a well-hidden web address. This creates a digital blind spot that attackers are quick to exploit.
Here’s how a typical QR phishing attack might unfold:
The victim receives an email or visits a website containing a QR code, which they scan using their mobile phone. This allows criminals to shift the attack from a PC, where security mechanisms are typically stronger, over to the mobile device. The QR code leads to a fake login page. The user enters their credentials on their phone, and just like that, the attacker gains access.
Over the summer, Telenor also observed several examples of voice phishing, a widespread and seemingly effective attack method. Initially, third-party CRM systems from Cisco and Google were targeted. Attackers call employees, posing as helpdesk staff. During the call, they persuade the employee to install remote access software, giving the attacker control of the PC. In other cases, attackers call the helpdesk pretending to be an employee, claiming to have lost their phone, forgotten their password, or needing to reset their two-factor authentication. More advanced attacks towards high-profile targets, have also used deepfake voices.
Neither QR phishing nor voice phishing directly exploits technical vulnerabilities. Instead, they rely on shifting the attack across devices or channels, bypassing traditional security controls that only monitor part of the chain. These attacks are also carried out in ways that can easily deceive even the most alert and security-conscious employees.
Attacks-as-a-service: Ready-made attack packages
The wide range of malware and information stealers available today shows that cybercrime has long since moved out of dark basements and into organised networks and professional platforms. Threat actors can easily buy access to these tools in the form of pre-built kits or attack packages, referred to as ‘attacks-as-a-service’.
This means that anyone with money and motivation can run a phishing campaign, commit fraud, or take over user accounts. The entire infrastructure is available as a service: phishing tools, email lists, design templates, domain registration, logs from information stealers, customer support, and even analytics tools for tracking conversion rates.
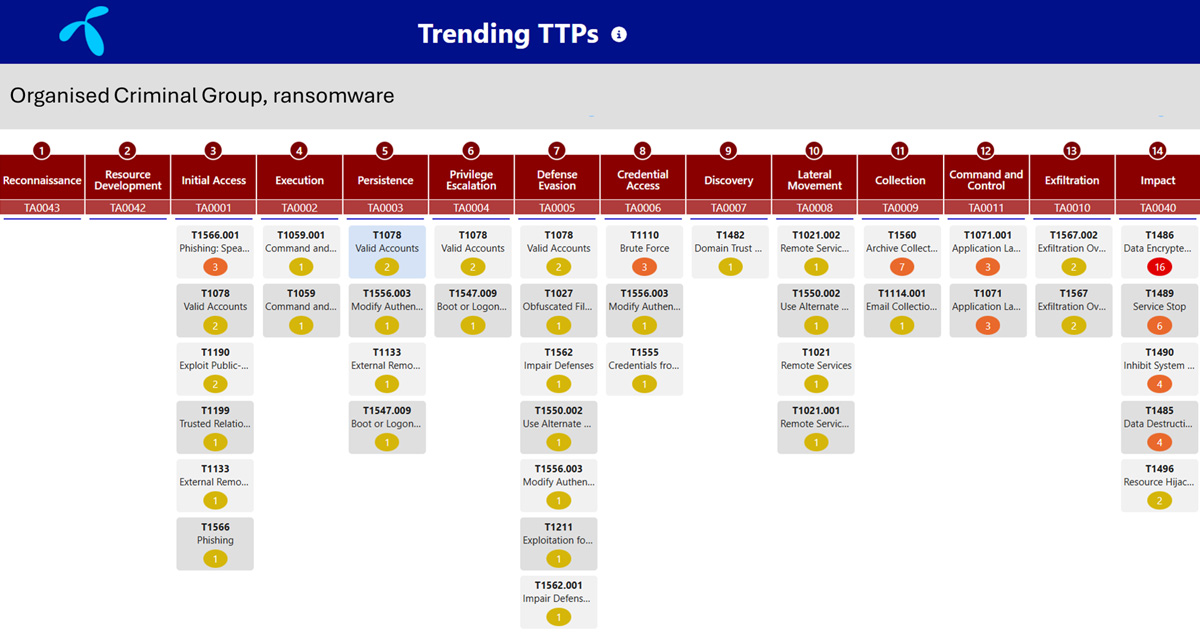
Criminals can browse menus of ready-made, off-the-shelf attack tools, which can also be customised to suit their needs. This makes fraud easier to scale and enables individuals with limited technical skills to carry out sophisticated attacks. You no longer need to know how to code, understand protocols, or identify vulnerabilities to target someone. All that’s required is access to the black market, often via Telegram or dedicated underground forums, and the resources to pay for the tools. See figure 1 for how Telenor correlates the modus operandi of criminal groups. By mapping their tactics, techniques, and procedures (TTPs), we can identify patterns that cut across incidents and geographies, allowing Telenor’s experts to anticipate likely next steps.
The availability of “attacks-as-a-service” contributes to the growing industrialisation of cybercrime. Those who previously engaged in minor offences, like selling counterfeit goods or manipulating ad platforms, are now selling access credentials, attack tools, and compromised accounts. And it’s not just businesses feeling the impact: individuals are increasingly affected through account takeovers, identity theft, and scams on social media.
Vulnerable supply chains and embedded malware
In recent years, we’ve seen increasingly sophisticated attack patterns, where even victims’ software solutions can become entry points into wider systems. Malware is disguised and embedded in well-known and widely used products, such as code, libraries, and other components.
In a supply chain attack, even the tools developers rely on to build software can be compromised. At this level, the attack is so deep within the supply chain that it’s virtually impossible for a typical organisation to maintain full visibility. The advantage for the attacker is that a single compromised link can grant access to hundreds or even thousands of organisations at once.
Malware often lies hidden in the source code and is only activated under specific conditions, for example, in a particular production environment or within selected companies. This stealth allows it to remain dormant and undetected for years, until it reaches its intended target.
The root of the problem lies in the dense web of dependencies between suppliers and customers. Complex supply chains are no longer the exception – they’re the norm across industries. A supplier’s supplier, or their supplier in turn, can suddenly become a weak point in an organisation’s security. As a result, many organisations are potential targets, simply because they may serve as a gateway to others.
Developers themselves are also more exposed to risk than one might expect. Much of this is due to long-standing traditions of open-source development and a culture of sharing and transparency. Code libraries and packages are often downloaded from open sources and run on infrastructure that may not be as closely monitored as central IT systems. This makes it possible for criminals to install malware without being detected.
In Norwegian DevOps, this represents a particular challenge, as many companies tend to reuse open components without having implemented adequate security measures.
AI agents and automated fraud
Artificial intelligence (AI) is, without a doubt, the most transformative factor in recent years when it comes to how digital attacks are designed and carried out.
In the past, it was easier to spot digital crime due to poor language and flawed visual presentation. With the help of AI, these attempts have become far more professionally executed. Images, video, and audio can be generated in seconds, and far less training data is needed than before. Attacks can now be tailored by language, industry, geography, and behaviour, increasing their effectiveness.
As AI develops at breakneck speed, well-resourced criminal actors are able to use the technology without regard for ethical principles, laws, or regulations. Much of this use mirrors how we use AI for legitimate business practices – automation, personalisation and efficiency – but with a criminal twist.
The year of the AI agent
AI agents have come into widespread use in 2025. An AI agent can be described as a programme that can carry out tasks independently, on behalf of a human. For example, it can automatically gather data, analyse it, and deliver on tasks. Multiple agents can even collaborate and divide tasks among themselves like a small digital team.
AI agents are useful for businesses, but they can also be misused by criminals. When large parts of the attack process can be delegated to AI agents, attackers become more efficient and capable of executing complex operations with fewer resources.
With the help of AI agents, criminals can now carry out fully automated, personalised, and highly convincing attacks, at record speed. These agents collect data, find email addresses, generate and send emails, harvest tokens, dig through data leaks, and log into networks – all without human involvement. The technology can even analyse what works and what doesn’t, adjusting tactics on the fly.
At present, fully autonomous, agent-driven attacks remain nascent, with few documented examples of actual use of such advanced systems – but it’s just a matter of time.
Increasing personalisation of attacks
Just as digital advertising and social media platforms build detailed profiles of individuals to target content and promotions, AI can be used to create a precise picture of a person based on cookies, behaviour, tracking, and data they’ve shared themselves.
AI agents can use that portrait to craft attacks tailored down to the smallest detail, based on who you are, what you’re interested in, and to whom you’re connected.
The more information a person has shared online, the easier it is to make the scam appear credible. This creates a troubling dynamic where, by sharing information, victims unknowingly feed the attackers’ tools with training data.
This level of personalisation makes attacks both more convincing and more effective, and therefore harder to detect and defend against, especially when it comes to large-scale campaigns.
AI is not just a threat – it’s also part of the defence
AI undoubtedly presents a major security challenge. Fortunately, the technology also offers new opportunities, both in defence and protection.
Advanced security filters, AI-driven analysis, and predictive models can identify and block fraud attempts before they reach their targets. Achieving this, however, requires continuous refinement of tools and sustained collaboration between technology companies, security providers, and public authorities.
For individuals, security still largely comes down to the same basic measures: verifying web addresses, using password management tools, and staying especially alert in situations where one is most vulnerable. Attackers will always seek out the weakest link in the chain, which makes human awareness and discipline as critical as technological safeguards.
AI amplifies risks but also multiplies defensive capabilities. In Telenor, by closely following how attackers leverage AI, we ensure that the organisation applies it strategically to strengthen our defences and maintain the upper hand.
When the tables turn: what do we uncover when our in-house hackers get to work?
– Insights from Telenor Cyberdefence, provider of advanced security services to businesses across the Nordics
Telenor Cyberdefence regularly conducts penetration tests for organisations that seek a realistic assessment of their cybersecurity posture. In simple terms, a penetration test is a “friendly break-in”, where we, with permission, identify security vulnerabilities so they can be addressed before threat actors exploit them.
Through hundreds of such tests, we’ve observed some clear patterns among Nordic organisations. Certain vulnerabilities appear with notable frequency, and in this article, we highlight some of the most common ones.
Misconfiguration: when systems generally function as intended, yet they’re set up in ways that introduce risk.
Outdated software and missing security updates: when a patch isn’t installed, the system remains exposed.
Passwords and authentication: improved with use of multi-factor authentication (MFA), but still a way to go
What can be done?
There’s no silver bullet when it comes to IT security, but we have made some practical recommendations based on what we observe in the organisations we work with:
Review access control regularly. Apply the principle of least privilege: users should only have access to what they genuinely need.
Invest in expertise around cloud services and secure configuration, especially in Azure and Active Directory.
Establish routines for security updates, and ensure all systems have clear ownership.
Enable MFA on all services that support it, and verify that it’s actually active.
Remove old users and accounts that are no longer in use.
Explore more security insights from our local experts
Telenor’s companies in the four Nordic markets offer their own security-related resources to help customers and stakeholders better understand the threat landscape and strengthen their defences. Go deeper in Telenor’s security world here:
Norway
Talk Security podcast series (Snakk om Sikkerhet, in Norwegian) – monthly episodes updating listeners on the latest within cybersecurity. Hosted by expert Rolv R. Hauge. Watch on Telenor Norway’s YouTube channel or listen through Apple Podcasts.
Finland
Cyber Criminals podcast series (Kyberrosvot, in Finnish) – a nationally and internationally recognized, award-winning podcast that uses a true crime format to raise awareness of cybersecurity threats. Listen here.
Denmark
How resilient are Danish companies? webinar (in Danish) – explores the state of corporate resilience in Denmark. Watch here
Seven ways to a more secure connection e-book (in Danish) – practical guidance for strengthening business and data security. Download here