How they attack

In the digital realm, the pressure that attackers exert on potential victims is constant. Criminals' motives vary: They may want money, trade secrets or other intellectual property, or perhaps they seek the attention that comes with disrupting a company's operations on a large scale. In this chapter, we take a closer look at attackers' methods and share our own experiences.
THE PREVALENCE of scam attempts today makes people hesitant to answer the phone when they receive a call from an unknown number. In this way, scams affect people who are not even direct targets.
Wherever someone turns in the digital space, there is steady pressure from criminals trying to deceive. They do this by using channels such as SMS, phone calls, social media, direct messages, websites, and competitions, as well as fake online ads that appear on otherwise credible sites. It only takes a moment’s inattention – perhaps when hungry, tired, or stressed – to click on a link one would otherwise avoid.
In economically uncertain times, we often see a surge in scam activities. When people are under financial pressure they are more likely to make poorer decisions, such as accepting offers or opportunities they would normally identify as too good to be true.
Those trends hold true in attacks against businesses. Phishing, CEO fraud and extortion attacks are among the most prevalent. In addition, we see distributed denial of service (DDoS) and other attacks that can partly be related to the war in Ukraine.
Hacking of private PBX (private branch exchange) systems is a well-known challenge that unfortunately is still relevant.
Remote access scams are on the rise
One type of scam, which is occurs quite frequently, involves calls that seem to originate from unknown Norwegian phone numbers. In these cases, the caller may impersonate a representative calling from a company like Amazon or some other large, well-known retailer or service provider.
These are criminals using programs designed to gain control of the target’s mobile phone: This is known as a remote access scam.
If the person targeted answers the phone, he or she usually hears a pre-recorded message informing them of a product order placed in their name, for example an iPhone. The message will direct them to “press '1' to get in touch with customer service”
or something similar. If they actually do so, they will instead be routed to a scammer.
Such phishing attacks usually come in waves: a surge of calls where the perpetrators pretend to represent, for example, Microsoft. Later, we could see a similar surge of calls allegedly from Amazon or from other different well-known companies.
No matter what company name the caller claims to represent, the approach is basically the same: The target receives a call and is presented with a problem. If it’s not a "wrongly purchased iPhone" it might be a “virus detected on x, y, or z device" or some other problem.
In each case, the scammer offers to help if the recipient follows the instructions given by the scammer. The scammer’s help is dependent on the victim downloading an app onto their mobile device or computer. The scammer often describes this program as a "security app" but, in reality, it's a tool that gives this criminal access to the victim’s mobile device or computer.
The app AnyDesk has emerged as criminals' preferred tool, but programs such as TeamViewer have also been misused. These are legitimate apps available as free downloads via both Apple App Store and Google Play. The problem is that they are also very easy to misuse. All that criminals need do is to convince a target – any owner of a mobile device or computer – to give them access. Time and again victims do so despite warnings in these apps about the risk of scams.
These remote access apps enable others to both see what someone is doing on their screen and remotely control that person’s Internet-connected device. If a person installs a remote access app and grants access to someone with malicious intentions, it is essentially the same as giving the criminal free scope to operate.
Once remote access has been granted, the possibilities of exploitation are many. Whatever the target sees on their own screen can also be seen by the perpetrator. If the victim logs into their online banking portal, the criminal can easily obtain the same information and access the account as well. Perpetrators can also capture one-time multi-factor authentication (MFA) codes sent via SMS, for example, and use those to hijack the victim’s account.
CEO fraud – still a serious threat
For the seventh year in a row, Telenor experts have deemed CEO fraud to be the scam method with the greatest loss potential for our company and subsidiaries.
In a CEO fraud, the criminal pretends to be a leader – usually the Chief Executive or other C-level executive – in a company. When successful, they target employees (often someone with financial responsibility and authority) and make them carry out a transaction that “urgently” needs to be completed.
Wherever someone turns in the digital space, there is steady pressure from criminals trying to deceive.
Criminals manipulate employees via email or text message and gather information they can use to create a false invoice, or otherwise trick the employee into making a payment. The criminals might instruct the employee to change an account number on an existing invoice to an account belonging to the criminals. Changes in payment information are also associated with the commonly used “business email compromise” (BEC) scam, in which the scammers gain access to an email account at the business or supplier.
Every year, we witness attempts to deceive employees at Telenor. In a recent attack, a sales director at Telenor Linx received an email marked “URGENT” signed by the CEO, which seemed to originate from the CEO’s email account.
The sales director, busy taking his children to school at the time, quickly replied that he could be reached via phone. Soon after, the requester replied: "I'm in an important meeting right now, and I cannot make calls. I need you to handle an urgent task for me carefully."
The sales director replied that he could clear his calendar until 2:30 p.m. To this, the response was: "Ok good. I want you to buy gift cards for certain customers. Can you do it in 25 minutes? Let me know so I can send you the names on the gift cards and the exact value of each. I will reimburse your money immediately after the meeting."
Only after the children were dropped off at school did the sales director take a closer look at the emails he had received, and then all the warning lights flashed. The message contained a number of grammatical errors and the tone of voice seemed different than usual. He knew these were typical hallmarks of a scam attempt. He contacted the CEO’s assistant and it was confirmed that the CEO had not sent the emails. Crisis averted.
In CEO frauds, criminals take advantage of the trust, respect, and sometimes, the fear that many employees have for senior officers. If the employee believes the CEO or a senior leader is actually behind a request, chances are that the employee will comply. The interaction might start with something as seemingly harmless as buying gift cards, but can escalate to involving much larger amounts once trust and communication are established.
In this case with the sales director, we cannot know for certain what the criminal was ultimately hoping to gain. Digital gift cards, as requested here, are known to be an easily tradable commodity on the Internet. The interaction might have ended with the gift cards. Still, it is quite possible that the first request would have been followed by other requests involving larger amounts.
Telenor’s own findings in recent years indicate that organised criminals to a larger extent are using open sources like LinkedIn and Facebook to map out employees and companies in connection with CEO fraud.
They combine this information with other open-source information. Once all the pieces are in place, the criminals can carry out targeted CEO fraud attacks with high precision. The more time scammers spend on information gathering and preparation, the more complex and believable their stories become. Thus, the amounts requested in these scams typically tend to be much higher.
In 2023, Telenor's security department followed up on several inquiries from our own employees who received suspicious inquiries and contact requests via LinkedIn. LinkedIn did not at this time require verification to link a user account to a company. Criminals take advantage of this. For example, they can claim to work at Telenor and use this to their advantage in direct messages to other Telenor employees on the platform.
More than 40 Telenor retail stores attacked – how we unmasked the hacker

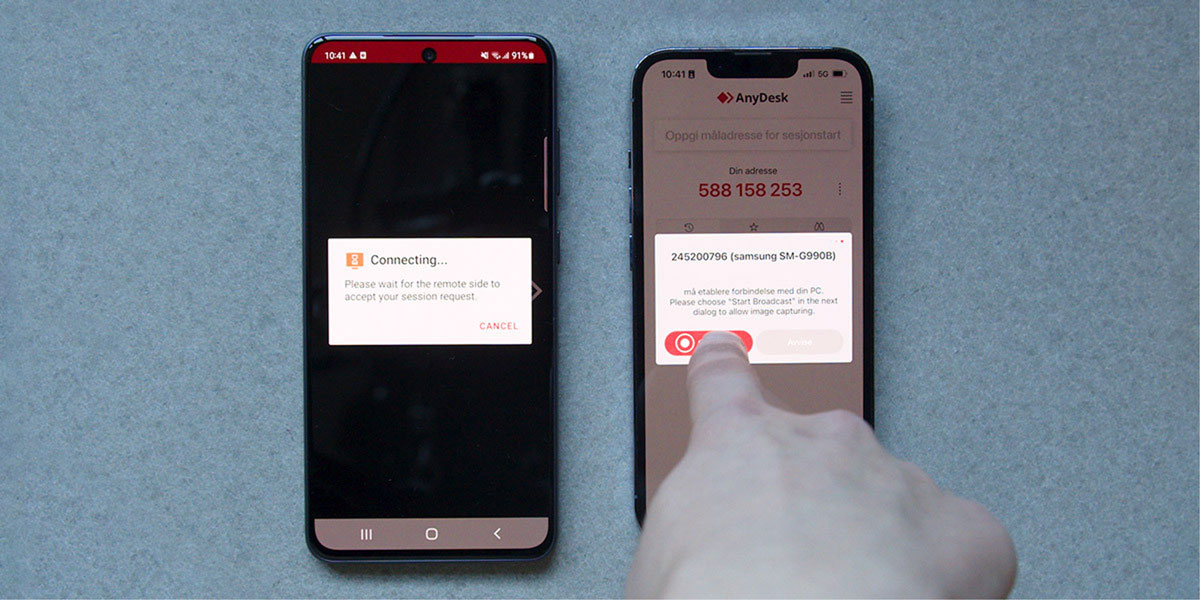
More than 40 Telenor stores received calls from the same number around the same time. This was a systematic attack, where criminals aimed to gain access to Telenor's data systems through phishing and social manipulation. Here’s what happened and how we figured it all out.
It started with an employee at a Telenor store in Oslo receiving a call, at work, from someone he initially thought was a colleague. However, he quickly realised something was wrong and ended the call.
Around the same time, another employee at a different Telenor store in Oslo received a call from a Swedish phone number. The man on the other end of the line claimed to be calling from Telenor’s IT support. He said he was calling about problems the staff had been experiencing with a printer in the store.
The caller sounded like a native Norwegian. The employee thought it odd that the person was calling from a Swedish number, yet at the same time, the call seemed genuine. Calls from support were not unusual, and the store had indeed been experiencing a problem with a printer. The employee, who happened to be alone at work when the call came through, deemed this a credible inquiry as he had previously reported to his boss that the printer near one of the cash registers was malfunctioning.
How the scam attempt unfolded:
Fake website and AnyDesk
After introducing himself, the caller explained that the printer trouble was due to a network error. To fix the problem, he needed access to the store’s systems and asked the employee to open the following website: Billett-Telenor.com.
The website looked identical to a Telenor site; however, it was fake. The hacker directed the employee to log into the site with his usual username and password for Telenor’s systems – which he didn’t have, as the Telenor retail store operated its own network independently from Telenor’s corporate system.
The hacker subsequently asked the employee to download AnyDesk. The employee was familiar with AnyDesk and knew it was a tool that allows remote control of one PC from another. But since the employee believed the caller was from Telenor, he thought it safe to allow access.
Within a few minutes the Telenor representative started to grow suspicious.
First, the employee noticed the browser warning that the URL was insecure. Then, he discovered that someone had created a new remote desktop on the PC, hidden behind the browser. He started to wonder if the man from Telenor support was doing other than what he said he was doing. When the hacker asked him to leave AnyDesk running overnight, his suspicions were confirmed.
The employee realised he had been tricked. The store was under attack.
The employee later said his first thought was “Oh no! What have I done?!” He knew that businesses are sometimes hacked but couldn’t imagine perpetrators being so professional.
Thinking quickly, he immediately uninstalled the application, deleted the file and turned off the PC. He called his operations manager and told him what had happened.
.webp)
Aware of the attack before the phone rang
What the employee didn’t know was that while he was talking to the scammer on the phone, Telenor had already actively been tracing the attacks against the Telenor stores. A dealer in Bergen had previously reported a phishing attempt where the scammers also pretended to be from Telenor’s IT support.
“When we received the first tip, we immediately started an investigation to determine the extent of the matter,” says Thorbjørn Busch, senior security advisor at Telenor.
The Swedish phone number turned out to be a real number connected to a Skype account.
Busch believes the use of a Swedish number may indicate that criminals are trying to find new methods to breach security. In 2022, Telenor introduced a block that prevents misuse of Norwegian landline numbers through “spoofing.”
Many companies have connections to Sweden, so a Swedish number in itself does not invite distrust. But the call coming from Sweden meant that Telenor would need to pursue the criminals abroad, making it more challenging to investigate the attack.
After an extensive search in traffic data on the Swedish number, the security team quickly saw which other Telenor stores had already been subjected to the phishing attack. After talking to some of the dealers, the team suspected that the perpetrators were trying to gain access to Telenor's other data systems via the Telenor stores – something that, fortunately, is not possible, Busch explains.
In this case, their first goal was likely to collect usernames and passwords via the fake website. When that did not go well, Plan B was to gain access to company information via AnyDesk.
The goal may have been to gain control over mobile numbers
It is still uncertain what the ultimate goal of the attack was, but there is no doubt that criminals can exploit such access for various purposes, with financial gain usually as the main goal. The criminals might have been hoping to achieve a SIM-swap. A SIM-swap can be used to gain access to the victim's accounts – for example, email or crypto wallets – by tricking a phone carrier into sending reset passwords or two-step MFA verification codes to the scammer instead of the actual account holder.
“This is not just a threat to individuals, but also to businesses. Full access to employees’ phone calls and texts can be utilised to access business intelligence, commit CEO fraud, or other types of attacks on the company,” says Busch. One possible theory is that this particular perpetrator wanted access to customer lists, with the hope of gaining control over mobile numbers on those lists.
Transparency is crucial to uncover fraud
At the second Oslo location, before the employee and his manager could even report the incident to Telenor, Telenor security contacted them. They were relieved to know that the problem was already in the security team’s hands. The case was handed over to the police, and although reports do not always lead to an arrest, they do provide the police with important information that may prove useful in other situations.
To be able to investigate such cases, Telenor is dependent on employees and managers reporting situations like these. When we ourselves manage to conduct a thorough investigation, chances that police eventually will make an arrest increase.
As to how the scammers could have known that the printer at the store was not working, unfortunately, that is a low-risk gamble no matter where they had called, says Busch, because printers are so prone to issues.
Spoofing – countermeasures and adaptive criminals
Telephone scams have become a serious social problem that unfortunately affects more and more people. Scammers who pretend to be bank representatives or police officers and take advantage of the trust we have in people in these professions. Their only purpose is to con people out of large amounts of money.
In recent years, we have seen an increase in cases where criminals have misused Norwegian phone numbers in scam attempts. What appears to be a call from a Norwegian phone number can actually be organised criminals operating from abroad. With simple measures, they are able to hide behind Norwegian landline numbers. Spoofing means that the original foreign phone number is replaced with a self-chosen Norwegian number.
After Telenor in 2021 introduced measures against spoofing of mobile numbers, we saw an increase in spoofing of Norwegian landline numbers. Landline numbers start with 2, 3, 5, 6, or 7 – and indicate a location, such as 21 80 21 80 for Oslo municipality or 75 55 50 00 for Bodø municipality. These are well-known number series with a high degree of credibility.
In addition to the calls that originate from abroad there has been an increase in scam calls conducted by Norwegian criminals over the past few years who come across as convincing with their polite and accommodating manners. The chances that someone will answer a call increase significantly if the number displayed on the screen is a Norwegian number, as opposed to a foreign or hidden one. Similarly, if the number belongs to a well- known company or public institution, people are even more likely to answer the call, and also more inclined to follow instructions.
In November 2022, several Norwegian telecom operators including Telenor joined forces and blocked criminals' ability to spoof Norwegian landline numbers. The initiative was the result of collaboration in the non-profit association ITAKT, which brings together Norwegian Internet and telecom operators to combat fraud and misuse of services and infrastructure. The blocking was implemented in line with recommendations from the National Communications Authority (NKOM) and guidelines set in Norwegian regulations for electronic communications and numbering.
This measure prevents spoofing of Norwegian landline numbers from abroad. If a call to a Norwegian number originates from abroad but displays a Norwegian landline number as the sender, it will be blocked and not reach Norwegian consumers.
What is spoofing?
Spoofing is a scam technique with false sender or origin information. The most common channels where spoofing occurs are email, text messages or phone calls where criminals forge a sender’s identity to carry out scam attempts. The technique is often used as part of a broader social manipulation attack, but spoofing of the source address for IP traffic is also used in some types of denial-of-service (DoS) attacks.
Even though landline numbers are less used by private individuals, they are still often used by businesses and public institutions such as the Norwegian Labour and Welfare Administration (NAV), the Tax Administration and the police. These agencies regularly experience their names and numbers being misused in scams. The block provides better protection against misuse for Norwegian businesses and public institutions.
Hacking of PBX systems – a continuous challenge
Telenor observes that business PBX systems are still subject to breaches. By exploiting weaknesses in the functions of the PBX, criminals can attempt scams. They can also use a PBX breach as a starting point for further cyberattacks, such as ransomware attacks.
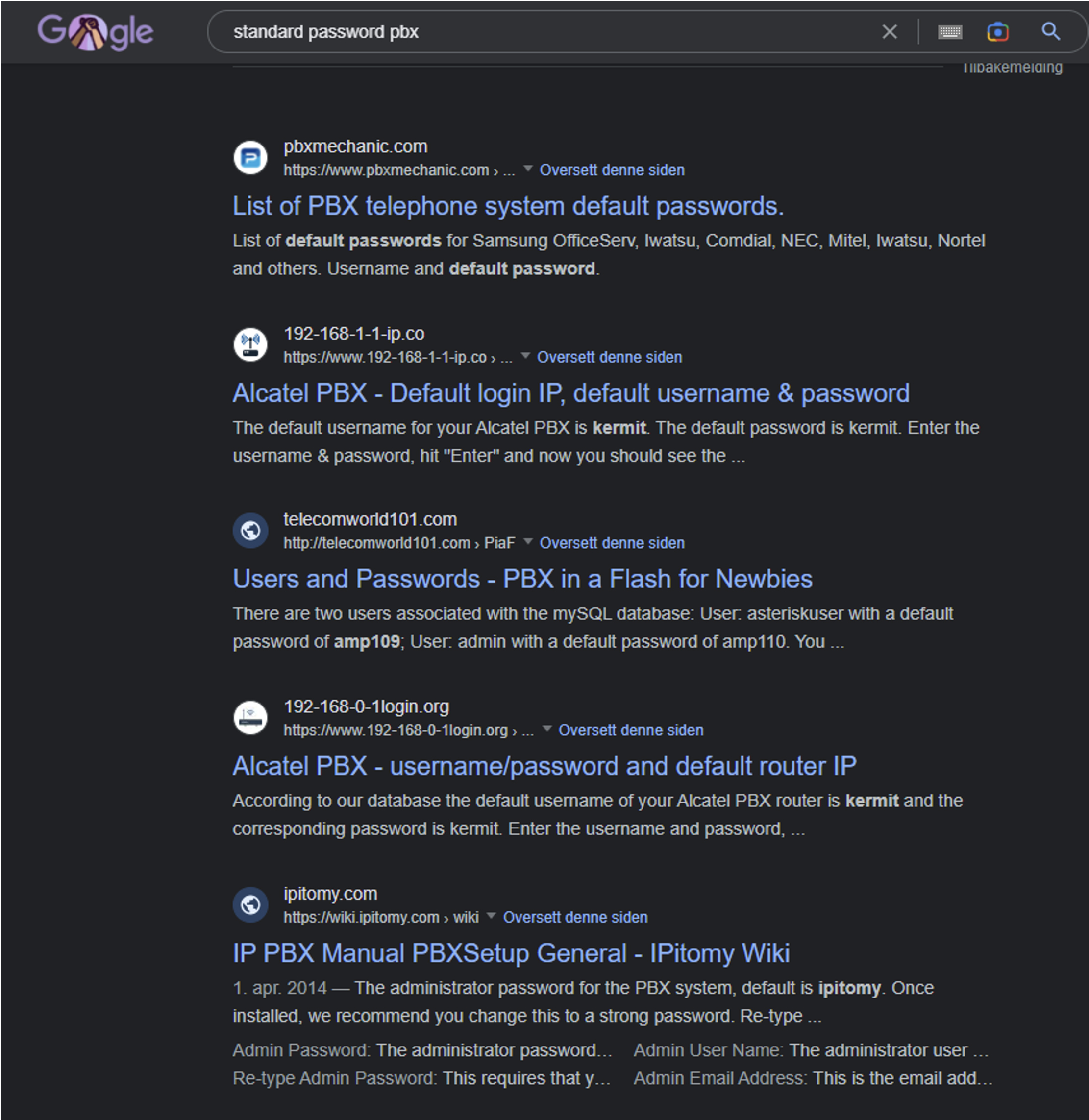
PBX systems are delivered with standard usernames and passwords and are connected to the Internet. If the username and password are not changed and the PBX is not secured at installation, the business exposes itself to significant risk. This can be compared to leaving one's house with the door unlocked. Changing standard passwords and settings is fundamental security hygiene, as lists of standard usernames and passwords are available on the Internet.
If criminals gain control of a PBX system, they can start searching for open international premium rate numbers (IPRN). These types of numbers are also called "international revenue share numbers.” Telecommunications carriers enter into agreements with other carriers for services like international calling. As such, the more minutes of calls to these IPRN numbers the criminals can generate from the PBX, the more money they can accumulate.
Scammers who pretend to be bank representatives or police officers take advantage of the trust we have in people in these professions.
Telenor has implemented measures to shut down access to IPRN numbers worldwide. Monitoring solutions have been used to identify this type of unwanted traffic in our network. The criminals typically use a script – referred to as a dialer – to automate searches for open premium rate numbers. They often have to make more than 1000 calls to various countries and numbers before they find open numbers. Telenor can often detect these attempts while in progress and start the process of shutting down this traffic before the scammers succeed. In this way we prevent further misuse. Our experience shows that by reporting the fraud to the police, we are able to stop payments related to such fraud in over 95% of cases.
This is why reporting fraud to the police is so important, even though Telenor can limit the financial damage by stopping further traffic. A report will also give the police a more comprehensive overview of this form of crime.
Premium rate numbers and wangiri fraud
Premium rate numbers are also used in so-called wangiri fraud. (Wangiri is Japanese for “one and cut.”) Scammers make money from wangiri calls by calling a number, letting it ring once, then ending the call. The victim sees that he or she has missed a call, calls the number back, and is put on a very long and expensive hold. By blocking calls to and from premium rate numbers used in scams, Telenor also prevents wangiri attacks against our customers.
The majority of premium rate numbers come from various national number series that are not generally used in the country or they could be technical series earmarked for specific purposes.
If, for example, you receive a call from the British Atlantic island of Ascension, and you choose to return the call, it's unlikely that your call will actually be answered in Ascension. It's much more likely that your call will be forwarded to a premium rate provider. Once the call is connected, you will hear an automated voice message (IVR) designed to keep you on the line as long as possible. "Please hold the line – your call is important to us."
Unfortunately, there are also a few local operators willing to pay commissions to premium rate providers for traffic to numbers in their networks. Here, it can be anything from individual numbers to entire series. Telenor blocks all such numbers as soon as they are identified.
Several companies offer services that, in practice, facilitate scamming. They provide necessary tools and services such as IVR servers, search tools and test numbers. They also supply numbers to criminals either directly or via other companies.
Telepremium is an example of such a provider (https://telepremium.net/how-it-works/).
Some of these companies also offer a downloadable phone app to check out which numbers are currently available. Contact with these companies is often only possible via Skype. They seldom operate with a physical address or company name.
Wangiri fraud and hacking of PBX systems are unfortunately just two examples of how scammers make money on premium rate numbers. There are others; any method that tricks the victim into calling the number and keeping them on the line for some time generates revenue for the scammers. Unfortunately, guidance and suggestions for different methods are also readily available online.
One of Telenor’s priorities is ensuring that traffic to and from such premium rate series is blocked and remains blocked. This is important.
Hacktivists carry out targeted and direct DDoS attacks
Over the past year, the number of DDoS attacks recorded through Telenor's systems has remained steady, with an average of around nine registered attacks per day. Most of the attacks target individuals and are relatively short-lived.
The majority of these attacks involve sending a large volume of data traffic to cripple the Internet connection of the target. Much of this traffic is generated by exploiting randomly misconfigured servers on the Internet to reflect and amplify traffic hitting the target. Since the traffic used in the attack originates from a misconfigured server, the attacker's actual IP address is effectively hidden.
Telenor and other major Internet service providers (ISPs) have systems that can effectively detect and stop these types of attacks. The systems monitor traffic on Telenor's routers that border other ISPs. This traffic comes from legitimate services but in far greater quantities than what is normal. Examples of services that are often misused include NTP (Network Time Protocol), DNS (Domain Name System), and LDAP (Lightweight Directory Access Protocol).
Following Russia's invasion of Ukraine, many hacktivist groups have emerged, both on the Russian and Ukrainian sides. On the Russian side, KillNet and NoName057 have been particularly active. These groups have also been mentioned in Norwegian media in connection with DDoS attacks. Over the past year, entities such as the Norwegian Labor Inspectorate, BankID, Altinn, NRK, Schibsted, the Norwegian Labour and Welfare Administra- tion (NAV), and the Norwegian National Security Authority (NSM) have been targeted.
The groups constantly change their targets and countries of attack, depending on what is reported by the media. For instance, Noname057 attacked Norwegian targets on March 2, 2023, following the Norwegian government's announcement of a multi-billion kroner financial support package to Ukraine.
Both Killnet and Noname057 coordinate their actions and discuss potential targets for attacks in chat groups on the messaging service Telegram. The latter uses a DDoS tool written in Python called DDosia, which is available for download through links shared in Telegram groups. Members register via a Telegram bot and are assigned a unique ID which they submit into the tool. The tool is installed on members' own machines, on hacked servers, or on rented virtual machines in the cloud. Those who contribute the most to the attacks can gain fame and, in some cases, small amounts of cryptocurrency transferred to their account as a reward for their effort.
In most cases, websites are attacked directly, with fully connect- ed TCP connections. This means that the connections are encrypted, making it difficult to discern from network traffic what is happening and what the attack traffic consists of. Before the attacks start, hacktivist groups thoroughly check their targets and find features on the websites of each target that typically burden the web server and underlying systems as much as possible. This is often combined with sessions that never disconnect, known as Slowloris attacks. When the attack targets the application layer, the attacked server can become overloaded without the network connection being filled with traffic.
The attack traffic consists of seemingly normal connections from regular users. Therefore, it is difficult to detect when a company is under attack using standard traffic analysis. These types of attacks are often only discovered when web servers under attack do not respond at all or respond very slowly. Sometimes, an increase in traffic is not even visible by analysing traffic graphs against the web server, but the attack can be recognised by looking at the number of queries or the resources being requested.
Since it is difficult to distinguish attack traffic from useful traffic at the network layer, this type of attack is often stopped using geographic IP filters. If a Norwegian website is under attack, for example, all incoming connections from outside the Nordic countries can be blocked. This type of blocking is obviously less suitable if the users of the website are geographically very dispersed.
To block DDoS attacks of this type, it is best to have access to the actual queries made against the web server. After analysing these, unwanted queries can be blocked directly on the web server, or preferably via a system before the server, like a proxy or a WAF (web application firewall).
Through logs and statistics, one can identify which resources on the server are being misused during the attack and block these. Systems that receive traffic from regular users should also be configured to prevent Slowloris attacks. This can be done, for example, by limiting the number of open network connections per client and how long they can be kept open, etc.
It is important to have an agreement in place with your ISP before an actual attack occurs to be able to stop DDoS attacks. Also, ensure that the web server's architecture has been thoroughly reviewed and that it is easy to access logs and block requests used in attacks.
Phishing – techniques and measures
For years, phishing emails have been one of the most commonly used methods for gaining illegal access inside an organisation. Having access to usernames and passwords of one or more employees in a company enables a hacker to misuse several ser- vices, among these, cloud-based services used by the company. According to the organisation Anti Phishing Work Group (APWG), 2022 was a record year for phishing, with more than 4.7 million attack campaigns worldwide. Since 2019, the number of such attacks has increased by over 150% per year.
Many companies train their employees to recognise phishing attempts and not click on suspicious links in emails. However, distinguishing genuine links from phishing proves difficult. Several companies use external providers for many of their internal services. This means that employees often must click on links to sites outside the organisation's internal domains, making it harder for employees to differentiate between legitimate and illegitimate links.
It is often difficult even for cybersecurity experts to determine what is a legitimate email or a scam. If a phishing test is conducted against a larger company, there will always be at least one employee who is tricked into giving away sensitive information such as usernames and passwords. Thus, attackers will achieve what they wanted.
To avoid attacks, several organisations in recent years have implemented various forms of multi-factor authentication (MFA). In addition to a regular password, users must enter a one-time code to log in. Attackers are increasingly circumventing this extra layer of security by also asking for the one-time code. The code can be manually entered on the mimicked service, or a proxy can be set up, enabling attackers to log in. In this way, unauthorised individuals can gain access to the victim's session key, thereby posing as the legitimate account owner.
An example of a commercially available service (PaaS, phishing as a service) that offers this functionality is "Greatness," as reported by Cisco Talos in May 2023. Greatness provides a complete phishing package with ready-made emails, phishing pages, proxy functionality and a control panel ready for use against services like Microsoft 365.
Authentication mechanisms resistant to phishing are required to secure against advanced attacks powered by malicious services like this.
Physical security keys, such as YubiKeys, are an example of an authentication method not vulnerable to phishing. A physical key is linked to the user's account and communicates via USB or Bluetooth with the device being used to log in. The key must be physically stolen to be used by unauthorised individuals for logging in.
Google introduced this type of security for its employees in 2017 and has not experienced successful phishing attacks since then. However, there is a significant barrier to adopting security keys. They must be distributed to users and registered, and they are also easier to lose, which would lock the user out until they obtain a new key.
A new technology offers security nearly as good as physical security keys, but without their drawbacks. This technology is known as passkeys and is based on the same standard as physical security keys. One such product is "WebAuthn,” developed by the Fast Identity Online (FIDO) security alliance.
Microsoft, Apple and Google now offer passkeys for logging in. Passkeys from these providers can also be used to authenticate the user further with other service providers.
Perhaps the dream of a password-free life without phishing attacks or password reuse will eventually become a reality.
A passkey consists of a private and a public key generated locally by the operating system of the device the user employs. The public key is shared with the service the user logs into. At login, the private key is unlocked locally on the machine; for example, by the user authenticating with facial recognition, fingerprint, or a PIN code. (Biometric information is not shared with the service the user is logging into.)
If adopting a new device, a new key can be generated on the new device by authenticating via an existing device, such as a mobile phone. The mobile phone will contact the new device via Bluetooth or NFC (near field communication) to verify that the user has physical control over the new device. Providers can also choose to synchronise passkeys between devices that the user is logged in on, as Apple does, for example, via Keychain.
Passkeys make phishing attacks impossible to execute. The address of the website the user is attempting to log into is exchanged encrypted with the service provider as part of the login process. In a phishing attempt, this address would be incorrect, and the login would be rejected. Unlike passwords, passkeys are also impossible to guess and consist of a long string of random data, in contrast to classics like "Password123!"
One of the biggest challenges with the solution is authentication if the user cannot log in, such as when they have lost their mobile phone. In such cases, the user must authenticate through an alternative method, such as another logged-in device, one-time codes printed on paper, a physical security key, pre-determined contacts who can confirm the user's identity, an SMS message, or by contacting customer service. These backup solutions must be designed to minimise the risk of users being permanently locked out, while ensuring that unauthorised individuals do not gain access to accounts by posing as the owner.
Going forward, passkeys will become more common for logins. Perhaps the dream of a password-free life without phishing attacks or password reuse will eventually become a reality.

KraftCERT: from the power sector's perspective
KraftCERT is a sector-specific response environment for the power sector working to prevent, detect and manage incidents in this sector.
Actors will continuously work to develop capabilities for destructive/disruptive attacks. The leak by the Russian company NTC Vulkan, which is a supplier to Russian authorities, clearly shows that Russian actors maintain a toolkit for cyberattacks. This toolkit can be used by threat actors, primarily state or mission-driven, for a fee. The toolkits also include tools for disruptive/destructive attacks.
The tools that NTC Vulkan has developed for attack purposes are well-planned. Several of them are modular, and some have also been demonstrated as functional. There can be several reasons why a threat actor might want to demonstrate a capability or tool, either to showcase tools to potential customers or to support state actors' claims about capabilities. However, even though certain capabilities are demonstrated, all actors, whether state or commercial, will not want to show their full capability. Instead, they want everyone to know that this is not their full capability.
Information from NTC Vulkan and the code for attack tools like PIPEDREAM are examples of leaks that are highly undesirable for threat actors, as their true capabilities are revealed to a great extent. Threat actors do not want others to have time to develop countermeasures. Conversely, all potential targets of attacks desire access to such information to prepare counter- measures.
The latest leaks demonstrate that threat actors are largely underestimated and are far more mature and professional in malware development than previous analyses have shown.
Long-term strategic planning of attacks against OT Attacking control systems is complex and requires more planning than attacks on conventional IT systems. However, attacks like Stuxnet and Trisis have shown that it is entirely possible. Even though the planning of such attacks takes time, the rate of change in OT is not high enough to necessarily pose a significant obstacle for threat actors.
In connection with Russia's attack on Ukraine in 2022, malware named "Industroyer2" was used. There is little doubt that the attacker had a significant amount of information about the target before the attack took place. The fact that planning takes time and that it must be custom-made for the target means that OT-targeted attacks are costly.
Other factors that make attacks costly are targets that are well-protected, such as the ones protecting high value systems, or those with strict regulatory requirements. The targets that are more difficult to access will be most interesting for advanced actors who have high competence, ample time and are willing to pay more for access and zero-day vulnerabilities. (An undiscovered weakness in an app or operating system is called a zero-day vulnerability; no security patch exists for it because the software creator is unaware of it and has there- fore had zero days to mitigate it.)
In such cases, threat actors will avoid exploring the open market for access, but will instead contact suppliers they trust. An access traded in a private forum will not appear on lists of known information leaks and will therefore remain hidden from the target.
To carry out successful attacks on control systems, detailed information about the systems is needed, including location. The owners of this type of information often underestimate how valuable it is, and in any case, information that is not documented as particularly sensitive may be poorly protected. It’s not just the owners who are targeted; it may be their suppliers as well. This was evident in incidents at Sargent & Lundy, which was storing documentation on 900 power stations it con- structed for customers when it was hacked in late 2022, and Black & McDonald, a Canadian government contractor which was presumably hacked for its military, power and transport documentation.
Attackers make between 50-500 login attempts each day over several weeks before hitting a valid username and password combination and logging into the system.
HelseCERT: From the health sector's perspective
HelseCERT is the national centre for cybersecurity in the health and care sector. The centre aims to increase the health sector's ability to detect, prevent and handle serious cyberattacks.
Attacks against the health sector
The security environment has changed significantly over the past few years. We see an increased intelligence threat, a sharp increase in activity from hacktivists and an ever-growing distance from Russia.
What has changed less is how threat actors attack. We have seen for a long time that known vulnerabilities, weak passwords and lack of multi-factor authentication are actively used to attack organisations. Attackers quickly start looking for vulnerable systems after information about vulnerabilities becomes publicly known. We continuously see attempts to guess usernames and passwords, and passwords that have gone astray are used to carry out attacks. Here we illustrate this with three different data breaches that occurred in the health sector in 2023.
Data breach 1 – vulnerable server online
A system with a vulnerable server was compromised by at least two different threat actors, both associated with ransomware attacks. The system was exposed on the Internet and had a publicly known vulnerability. The first attacker was stopped by antivirus software and gave up. The second was not stopped and managed to gain administrator access, moving on to several servers, including domain controllers, file servers, database servers and more. The vulnerability was exploited shortly after it became publicly known. The attack was discovered after about three weeks. The organisation's IT systems were taken offline for about two days when the attack was detected, and much time and resources were spent on analysis and cleanup afterward.
Data breach 2 – unauthorised access to VPN solution
A weak password on a VPN solution allowed the attacker to log into a lab environment by guessing usernames and passwords. The attacker connected to a VPN tunnel for about five minutes. Through this tunnel, they could access several systems further inside the organisation. Analysis of log data does not suggest that the attacker did more than confirm access. It is assumed that the attacker planned to return later.
Data breach 3 – password guessing and a vulnerable server
A ransomware group is assumed to be behind this data breach. The attacker started with brute force activity (password guessing) against a server. They used about 400 generic usernames and various passwords to guess the correct ones. They made between 50-500 login attempts each day over several weeks before hitting a valid username and password combination and logging into the system. After logging in, they exploited a known vulnerability, for which a patch had not been installed, to install a program that allowed them to remotely control the server. The attack was discovered by a third party who noticed suspicious traffic from the compromised server. Quick incident response stopped the attack with no major consequences.