
Threat intelligence driven defendable architecture is the concept Telenor uses to develop its security architecture. This concept is the foundation for the guiding documentation on which the security uplift program was run from 2018 to 2019 and security architecture in the Telenor Group as a whole.
But what does it actually mean? What is the thought process behind it? How is it applied and implemented? This second article in our series will cover the core concepts and design process for the design phase of defensive security controls and their ability to mitigate multiple levels of threats.
Defendable Architecture as a concept is how to design, build, operate and defend an infrastructure while continuously applying threat modelling and analysis during each of the process steps in a continuous lifecycle. In order to enable a targeted and focused approach for implementing security, one must identify what assets to defend and what defensive controls to implement. It’s crucial to base this on the threat actors’ mode of operations and preferred methods of attack.
The figure below shows the methodology that is used by LHM for threat analysis, Telenor utilises a similar approach combining the process from LHM with other industry standard threat modelling methodologies.
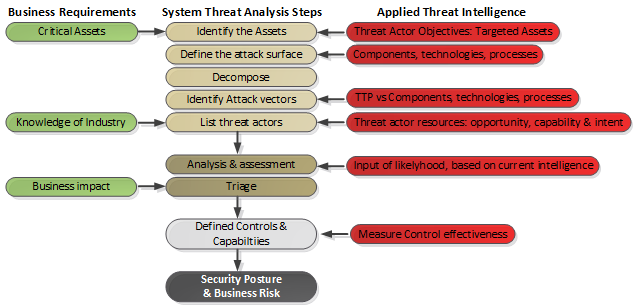
The first step to conduct when beginning a threat model process is to decide what assets are important for an organisation to defend since not all components of an organisation are equal. The key to a successful business-driven architecture is to protect what is important in an efficient way, as opposed to attempting to protect everything at the same time (and most likely fail).
Assessing each individual asset should be done from a business perspective and the value of each asset should be based on the money and effort of purchasing it, setting it up, and creating the information that is stored within it. Weightage should also be applied to the business criticality of the asset since all assets are not equal to an organization. i.e the corporate website is important but less important than a sales organisation’s Customer Relations Management (CRM) system.
Once the organisation’s critical assets are identified, they should be analysed and broken down into their individual technology components to identify attack surfaces and vulnerabilities, so that a clear picture of potential threats can be built.

An important part of the threat-modelling process is to know about the threat actors themselves. To understand the threat actors, such as their motivations, goals, and in particular their methods – The latter is often referred to using the common term Tactics, Techniques, and Procedures (TTP). Threat intelligence information gathered about the attackers and their methods is then applied to the identified attack vectors and assume vulnerabilities, another concept referred to as threat modelling.
Threat modelling defines the types of risks and threats an organisation would be facing and the needed controls to mitigate them based on business impact and likelihood. Each organisation would need to apply threat modelling individually, based on what sector they are in, the information they process and store, the technology they are using in their IT infrastructures, their size etc. For this purpose, there are several readymade methodologies available such as Microsoft’s STRIDE for threat modelling and DREAD for risk assessment, or PASTA, which is a seven-step process aimed at aligning technology and business objectives.
So let’s look at the assumed opposition. The threat actors have been classified into six tiers based on their capabilities, potential for damage, and their available resources. Keep in mind that this is a generalised view. There may be threat actors that have significantly better (or lower) capabilities than their generic “label” suggests, but the tiers described below give an assumption of what to expect as an average.
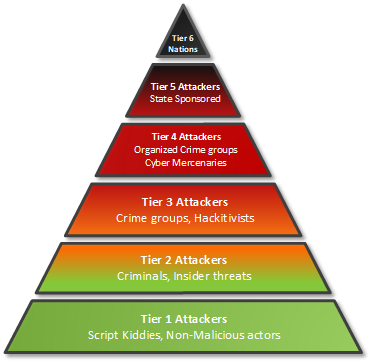
Tier 1 consists of non-malicious actors and so-called script kiddies. They possess limited capabilities, reusing tools, and techniques handed to them from other threat actor tiers or discovered on the internet. These are mostly of a more exploratory nature but they may occasionally get access to powerful tools.
Tier 2 is criminals and/or insider threats with an overtly malicious intent to damage. Mostly singular or low in number and depends on known exploits and well-known techniques.
Tier 3 is crime groups and hacktivists. This is the first level of the more advanced threat actors. They usually operate in groups and have access to previously unknown vulnerabilities, making them more dangerous than the lower tiers. Their motivations are often political or seeking to focus knowledge on a certain topic. They focus on destruction such as distributed denial of service and defacing of websites but are not shy about exfiltrating and publishing information harmful to their target.
Tier 4 is organized crime groups and cyber mercenaries. They are the mafia groups of the internet. Mostly motivated by profit, their actions can include ransomware or outright digital theft such as breaking into bitcoin exchanges or finance networks, extracting credit card information by the millions. These actors usually always operate in groups and can build and use sophisticated attack infrastructures to utilise unknown vulnerabilities. Often these actors will seek business-related information that can be sold to other third parties, whether it be contract documents, customer databases, or intellectual property.
Example of a tier 4 threat actor attack: Target – how cyber criminals bypassed the defenses of retailer Target and ran off with the details of 40 million credit cards.
Tier 5 is the first level of so-called advanced persistent threats (APT). Often directly sponsored by nation states, APT groups have significant resources available to pursue targets that are usually of strategic importance. These actors work with a specific target in mind and will pursue relentlessly until their goals are achieved, using unknown and sophisticated multi-stage attacks. It is not uncommon to experience a previously evicted APT group return into the network through a new way, just weeks after the initial removal. The group often targets customer information, such as information stored in data warehouses, user accounts, or telecom related data such as call data records and location data about specific people.
Example of a tier 5 threat actor attack: NotPetya – how stolen US cyber weapons lead to the most devastating cyber attack in modern history.
Tier 6 is the most advanced of the threat actor group. These are the intelligence agencies and offensive capabilities of a country’s cyber military. They have, to a large degree, the same mode of operations as the sponsored APT groups, using very advanced techniques, being capable of creating new vulnerabilities on their own, and working with a specific geo-political target in mind. The difference is the number of available resources that this tier has available for its operations, potentially assigning 100+ people to an operation towards a target in multiple stages. These actors’ motivations range from espionage, IPR theft, political manipulation, tracking dissidents in other countries, and tapping into the communication of national governments.
Example of a tier 6 threat actor attack: Belgacom – how British intelligence services compromised Belgium’s largest telecomms operator.
By combining so-called threat intelligence (both internal information from the monitoring of own infrastructure and external information from threat intelligence feeds) and knowledge about the organisation’s critical assets and threat modelling, it’s possible to make assumptions around the levels of threat actors that are most likely to attack the organisation and how it will be done. Understanding what makes up their relevant threat potential is key to apply the “right” level of defensive controls. The threat mitigation must also take into account regulatory requirements, business requirements, what scope of the organisation’s assets it applies to, and the organisation’s level of risk appetite.
Knowledge about attackers and their techniques are also commonly shared between different telecom operators or other large organisations in the context of collaborative organisations such as FIRST. Threat actors attack across sectors and industries. Therefore, any information that could help identify and narrow down potential threats should be considered and applied through the threat intelligence phase, when analysing the different defensive controls during the different stages of their life-cycle.
The Mitre ATT&CK framework is a global knowledgebase of threat actor tactics and techniques based on real-world observations. It does not focus on the tools and malware, but how the threat actors interact with the systems. It is organised by grouping techniques into sets of tactics to give context and provides an excellent methodology by mapping out attack methods at different stages. It shows how initial access, persistence, defensive evasion, lateral movement, and exfiltration are conducted and what techniques are commonly being used at each individual stage. Combined with the information about the critical assets themselves in the form of surrounding network configuration, running software, behavior, etc., a relatively precise picture can be drawn of potential weak spots in the defensive infrastructure. With maturity, it is possible to develop so-called indicators of compromise (evidence of un-authorised activity) to detect attacks in early stages.
Based on the assessment of threat actors and the identified assets, various attack vectors and security controls can be defined and implemented in the most efficient way. A framework highlighting 14 key defensive controls with an incremental level of implementation helps in creating the right level of security posture for an IT infrastructure deployment. Similarly, one can use the different defensive controls along with their definitions to measure the organisation’s current implementation and assess the effectiveness of the overall security posture. Combining the two, of assessing the current set of implemented controls and defining what threats should be properly mitigated, a gap analysis along with a roadmap on how to gradually reach the desired level of controls can be developed.
When studying the history of warfare and conflicts around globally, none of the conflicts are exactly the same but still, there are some similarities between them in the forms of strategies and tactics which have been proven over time to be rather effective. In the world of cyber warfare (which threat actors for all practical purposes are conducting) the principles are the same. A threat actor will not put considerable energy into creating a new vulnerability unless they have to. They will instead often use common and known techniques that are already proven to be effective, whether is malware, phishing or exploiting an already widely known vulnerability.
In particular, the more advanced threat actors usually will save their most powerful shiny tools and techniques if they can use a much simpler way into an organisation’s network. Identifying their methods throughout the multi-stage process of a break-in is key to defining the different actor vectors available for a threat actor.
While primarily focusing on the technology aspects of security, defendable architecture and the defined defensive security controls also map directly into the tools and capabilities that are required for a security operations team to provide an efficient incident response. This also helps define the overall security maturity of an enterprise. People need useful tools, and the tools need competent people to operate them. Only then will the security be at a level where confidentiality, integrity, and availability are assured while connecting you to what matters most.